Businesses have now come to understand the importance of backing up data to avoid the negative impact of data loss on their operations. Data loss can happen through multiple scenarios. It could be disruptions caused by accidental deletions, hardware failure, or more severe accidents like natural disasters or malware attacks.
We may think one copy of crucial data is sufficient to recover from. However, at the core of every sound data recovery plan is the 3-2-1 backup rule. In recent times, this rule has become a universally accepted strategy within the IT world and beyond. The 3-2-1 backup approach is recommended by information security professionals and government agencies like the Cybersecurity and Infrastructure Security Agency (CISA) in the USA (in the Data Backup Options document by US-CERT).
Please keep reading to learn more about the elements of the 3-2-1 rule and how to blend it with your backup ecosystem to meet emerging cybersecurity challenges.
Before we start,
The 3-2-1 backup rule is the one thing to live along. At Zmanda, we have been promoting this concept for many years in order to assist enterprises in ensuring recoverability at critical times. Get the Free Trial now!
What Is the 3-2-1 Backup Rule?
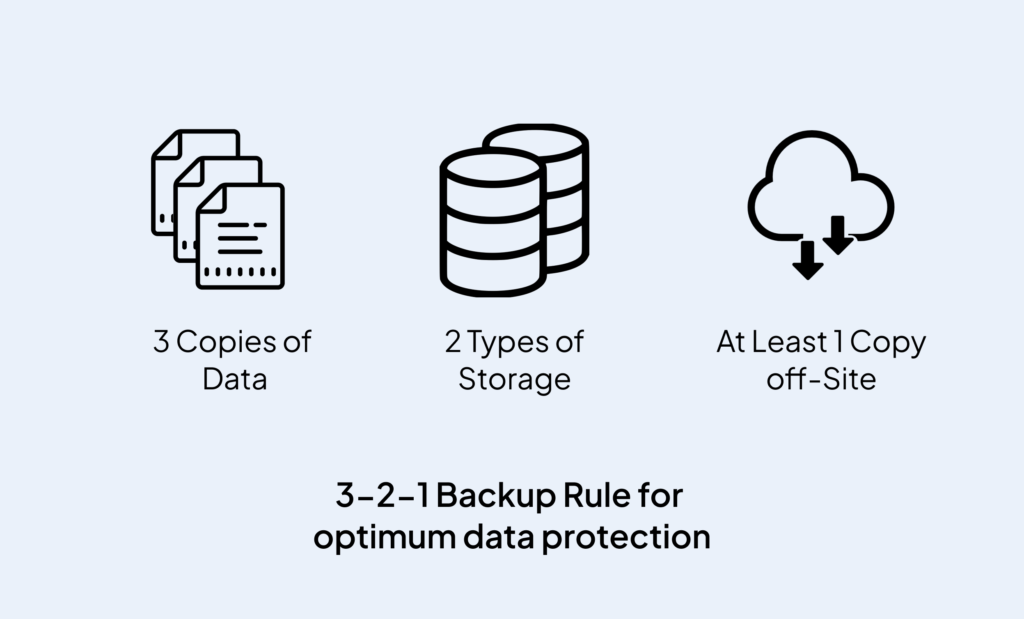
The 3-2-1 rule states the following:
- Make three copies of the data
- Store it on two distinct media.
- With one copy kept off-site.
American photographer Peter Krogh was the one who first came up with the 3-2-1 rule. It was a very significant innovation for the photography industry that has broad consequences for other technological fields and is still relevant today.
Using this base rule outline, we can now update it to work with modern critical data. But let’s not overlook the advantages of the base rule:
- It does not require any particular hardware or technology.
- Almost any failure scenario can be addressed.
This approach is not about choosing one medium over another but rather about finding the right combination of storage media and locations in terms of cost-efficiency, security and flexibility. Let’s take a closer look at each point of the 3-2-1 rule.
How to Use the 3-2-1 Rule With Zmanda?
In the scope of Zmanda’s data backup and ransomware protection, this rule is touted as a solid place to start with. Some of the most basic applications of the 3-2-1 rule are as follows:
- Make at least 3 copies of data to avoid single-point failure: Three copies mean the primary production data and two backup copies. Keeping 3 copies of data is the bare minimum required to ensure that you can recover in any failure scenario, keep recovery objectives low and avoid a single point of failure.
- Store it on two different media to exclude storage media defects: Having all your backups on the same type of storage media makes it more likely that both devices would fail at about the same time due to a defect or simple wear and tear.To abide by the 3-2-1 rule, you need to store your primary data and backup copies on at least two different storage media, including internal or external hard drives, NAS, tape, and others.
- One copy kept off-site for an extra layer of security: The 3-2-1 backup strategy dictates that you should store one or more backup copies in a remote location, for example, in another city, state, country, or even continent. This way, even in times of adversities like theft, software malfunction, human error, or a local disaster, one copy that’s in a different location can be salvaged. A remote location in this case can be physical off-site storage or the cloud.
Note: In the ransomware era, it’s a good idea to add another 1 to the rule where one of the media is offline.
Keep in mind that while remote backups improve your chances of recovery, keeping local copies provides faster and easier recovery. The 3-2-1 backup rule should be part of an extensive disaster recovery plan to ensure business continuity and prepare for all potential risks.
Pro Tip: The more backup copies you have, the less likely it is that you would lose them all at once. Having a single backup stored in the same location as the primary data means that any disaster that hits your production can also affect your secondary copies.
This actually exceeds the requirements because it uses three separate mediums. It’s important to note that some people prefer not to include the production data as a copy in the 3-2-1 Rule. This indicates that of the 2 additional copies, the varied media is a requirement and the variety of restoration needs to be taken into account.
In this fast-changing era, organizations nowadays prefer having the most critical data sets with 4 copies where the production data is also included.
How to Achieve the 3-2-1 Rule?
Zmanda’s ability to crank up so many variations of the 3-2-1 rule is one of our favorite aspects of being a software vendor with a strong lineup of partnerships. Zmanda is quite adaptable, and each of the following applications would count towards the 3-2-1 rule configuration:
- Supports backups on reliable and straightforward disk storage
- Supports long-term data archival with tape storage
- Supports backups on NAS and SAN devices
- Backups on removable storage
- Backups in object storage such as in the public cloud
- Backups in cold archive storage in the public cloud
- Backups hosted or managed by a service provider
3-2-1-And-Go With Zmanda!
The 3-2-1 backup rule has been the most effective approach in data protection for decades. As threats continue to evolve, so should your security techniques. With Zmanda, keep your backed-up data secure and segregated, preventing malicious encryption and deletion during a ransomware attack. This allows you to recover your production servers, databases, applications, and workstations quickly and seamlessly.
You cannot implement a comprehensive data protection plan without a modern solution like Zmanda Enterprise Backup & Recovery Solution. Get the Free Edition today to implement these strategies in your environment.


