The ZMC comes with SSL certificates that have a defined expiration date. If the certificates reach their end of validity, you may encounter problems when conducting routine tasks such as adding new backups, restores, clients, and storage systems.
This KB is applicable only for Zmanda versions 4.0,4.1, and 4.2
- The validity of the certificates can be verified by the following method.
- Using the following 'openssl' command from the server command line.
sudo openssl x509 -in /var/lib/amanda/.tlsv3_zmc.crt -text -noout | grep -i validity -A2
sudo openssl x509 -in /var/lib/amanda/.tlsv3_aee.crt -text -noout | grep -i validity -A2
If you observe that the validity of the certificates has expired, you can follow the procedure given below to generate new certificate files.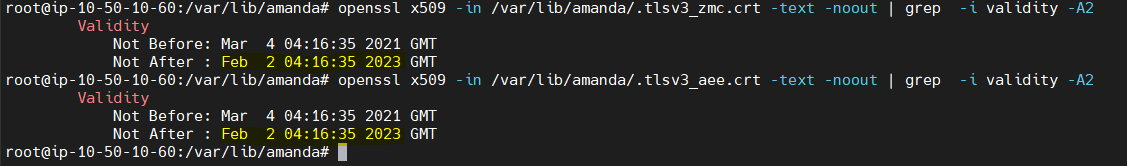
- Using the following 'openssl' command from the server command line.
- To generate the key and certificate for zmc_service
You can either execute this script, or follow the steps below:- Switch to amandabackup user on the server.
su amandabackup
- Create a new directory to generate the cert and key files. Make sure to execute all the subsequent commands from within this directory.
mkdir -p /var/lib/amanda/tmpcerts
cd /var/lib/amanda/tmpcerts - Generate a new Certificate Authority (CA):
/opt/zmanda/amanda/bin/openssl ecparam -name prime256v1 -genkey -noout -out tlsv3_ca.key && /opt/zmanda/amanda/bin/openssl ec -in tlsv3_ca.key -pubout -out tlsv3_ca.pkey
/opt/zmanda/amanda/bin/openssl req -new -x509 -days 365 -sha384 -addext "keyUsage = critical, digitalSignature, cRLSign, keyCertSign" -key tlsv3_ca.key -out tlsv3_ca.crt - Create a new file named 'zmc.conf' and copy the following contents into the file. Replace the <Bold> content with your organization information.
[req]
prompt = no
default_bits = 2048
default_md = sha512
distinguished_name = req_dn
[req_dn]
commonName = <hostName>
organizationName = <MyOrganization>
organizationalUnitName = <MyOrganizationDeppartment>
emailAddress = <MyOrganizationDeppartment_Email>
countryName = <MyCountry2LetterInternationalCode>
stateOrProvinceName = <MyState>
localityName = <MyCity>
[v3_ssl]
basicConstraints = critical, CA:FALSE
nsCertType = server
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[v3_mtls]
basicConstraints = critical, CA:FALSE
nsCertType = client
keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = clientAuth
subjectAltName = @alt_names
[alt_names]
IP.1 = <hostIP>
DNS.1 = <hostName>
DNS.2 = h<hostIP replacing dots (.) with dashes (-)>.server.betsol
# sample of above= h192-168-1-2.server.betsol
# see x509v3_config for other extensions - Generate new ZMC TLS certificates for Web interface.
/opt/zmanda/amanda/bin/openssl req -newkey rsa:2048 -nodes -keyout self-signed.key -x509 -days 730 -out self-signed.crt -config zmc.conf -extensions v3_ssl
- Generate new ZMC certificates for mTLS communications.
/opt/zmanda/amanda/bin/openssl ecparam -name prime256v1 -genkey -noout -out tlsv3_zmc.key && /opt/zmanda/amanda/bin/openssl req -new -sha384 -config zmc.conf -extensions v3_mtls -key tlsv3_zmc.key -out tlsv3_zmc.csr
/opt/zmanda/amanda/bin/openssl x509 -req -days 730 -sha384 -extfile zmc.conf -extensions v3_mtls -CA tlsv3_ca.crt -CAkey tlsv3_ca.key -CAcreateserial -in tlsv3_zmc.csr -out tlsv3_zmc.crt - Copy and replace generated files into the ZMC server.
cp tlsv3_ca.crt /var/lib/amanda/.tlsv3_ca.crt
cp self-signed.key /var/lib/amanda/.self-signed.key
cp self-signed.crt /var/lib/amanda/.self-signed.crt
cp tlsv3_zmc.key /var/lib/amanda/.tlsv3_zmc.key
cp tlsv3_zmc.crt /var/lib/amanda/.tlsv3_zmc.crt - Verify the ownership and permission of the copied files. All files should be owned by 'amandabackup' user and group with the following permissions.
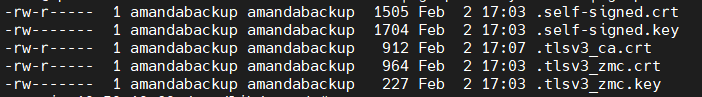
- Switch to amandabackup user on the server.
- To generate the key and certificate for aee_service
- Create one folder per each AEE server that you have.
mkdir aee1
cd aee1 - Create a new file named 'aee.conf' and copy the following contents into the file. Replace the <Bold> content with your organization information.
[req]
prompt = no
default_bits = 2048
default_md = sha512
distinguished_name = req_dn
[req_dn]
commonName = <hostName>
organizationName = <MyOrganization>
organizationalUnitName = <MyOrganizationDeppartment>
emailAddress = <MyOrganizationDeppartment_Email>
countryName = <MyCountry2LetterInternationalCode>
stateOrProvinceName = <MyState>
localityName = <MyCity>
[v3_ssl]
basicConstraints = critical, CA:FALSE
nsCertType = server
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
IP.1 = <hostIP>
DNS.1 = <hostName>
DNS.2 = h<hostIP replacing dots (.) with dashes (-)>.server.betsol
# sample of above= h192-168-1-2.server.betsol
# see x509v3_config for other extensions - Generate new AEE certificates.
/opt/zmanda/amanda/bin/openssl ecparam -name prime256v1 -genkey -noout -out tlsv3_aee.key && /opt/zmanda/amanda/bin/openssl req -new -sha384 -config aee.conf -extensions v3_ssl -key tlsv3_aee.key -out tlsv3_aee.csr
/opt/zmanda/amanda/bin/openssl x509 -req -days 730 -sha384 -extfile aee.conf -extensions v3_ssl -CA ../tlsv3_ca.crt -CAkey ../tlsv3_ca.key -CAcreateserial -in tlsv3_aee.csr -out tlsv3_aee.crt - Copy the generated files to /var/lib/amanda directory
- If both ZMC and AEE are hosted on the same server, use the below commands.
cp tlsv3_aee.key /var/lib/amanda/.tlsv3_aee.key
cp tlsv3_aee.crt /var/lib/amanda/.tlsv3_aee.crt - If AEE and ZMC are hosted on different servers, then use 'scp' to copy the files to the AEE server - (optional).
scp /var/lib/amanda/tmpcerts/tlsv3_ca.crt user@<aee1_IP>:/var/lib/amanda/.tlsv3_ca.crt
scp /var/lib/amanda/tmpcerts/aee1/tlsv3_aee.key user@<aee1_IP>:/var/lib/amanda/.tlsv3_aee.key
scp /var/lib/amanda/tmpcerts/aee1/tlsv3_aee.crt user@<aee1_IP>:/var/lib/amanda/.tlsv3_aee.crt - If you have more than one AEE server, create separate folders for each AEE server, like in step 3(a) - (optional).
cd /var/lib/amanda/tmpcerts
Repeat steps 3 (b) and 3(c) to generate AEE certificates. Then use 'scp' to copy the files to the second AEE server.
mkdir aee2
cd aee2scp /var/lib/amanda/tmpcerts/tlsv3_ca.crt user@<aee2_IP>:/var/lib/amanda/.tlsv3_ca.crt
scp /var/lib/amanda/tmpcerts/aee2/tlsv3_aee.key user@<aee2_IP>:/var/lib/amanda/.tlsv3_aee.key
scp /var/lib/amanda/tmpcerts/aee2/tlsv3_aee.crt user@<aee2_IP>:/var/lib/amanda/.tlsv3_aee.crt
- If both ZMC and AEE are hosted on the same server, use the below commands.
- Verify the ownership and permission of the copied files. All files should be owned by 'amandabackup' user and group with the following permissions.
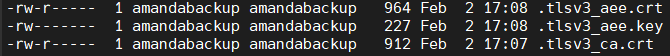
- Create one folder per each AEE server that you have.
- Restart the ZMC and AEE services as the 'root' user
systemctl restart run-zmanda-backup-server.service
systemctl restart run-zmanda-zmc.service
If you also want to solve the certificate warning shown by the browser when loading the Zmanda Web Console, you can download the ‘tlsv3_zmc.crt’ file on your PC and install it into your browser's trusted server certificates.
Please reach out to Zmanda Support if you are facing any issues.
